Learn how hackers view your infrastructure
Download our latest webinar
Watch world-renowned cybersecurity experts Ymir Vigfusson (Keystrike) and Paula Januszkiewicz (CQURE) go on a journey into the mind of hacker. Learn about common attack types used to exploit vulnerabilities and penetrate your infrastructure, and what they can do once they’re inside. Stay up to date on the techniques you can implement to keep hackers out of your life.
Typing proves that you are real
Zero-friction controls against lateral movement
Keystrike secures user sessions, working seamlessly with existing authentication mechanisms, to ensure they are not supplanted, stolen, or sneakily harboring stealthy attackers. Keystrike guarantees that all commands were physically typed on an employee workstation, seamlessly stopping stealthy attackers from misusing remote access connections.
Protect your legacy systems with Sanctum Guard
Safeguard your high-privilege users
Secure remote workers and work-from-home jump boxes
Ensure integrity for contractors accessing your network
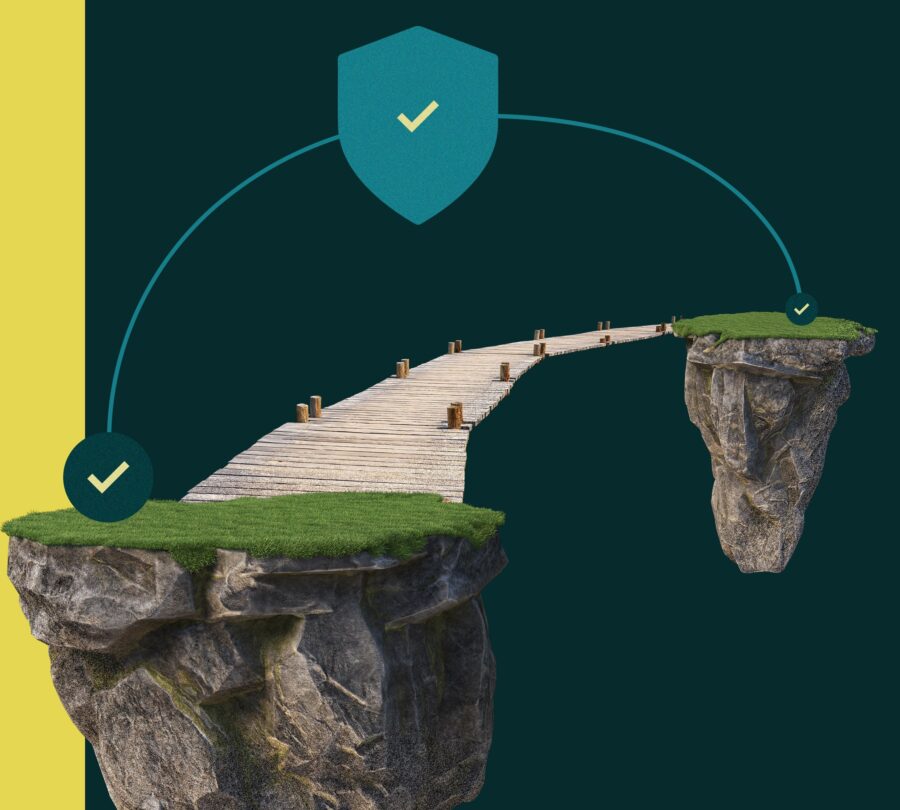
Even though important systems are firewalled away, we still need bridges to those islands. Keystrike Sanctum Guard protects these sensitive bridges by ensuring only your own employees are sending commands across.
Augment your security stack
Complementary controls for your zero trust environment
Keystrike secures user sessions, working seamlessly with existing authentication mechanisms, to ensure they are not supplanted, stolen, or sneakily harboring stealthy attackers. Keystrike Sanctum Guard protects remote access connections, while Keystrike Cloud Protector (forthcoming) adds integrity to web sessions.

Phishing attacks
MFA and security keys don’t help when the computer is compromised: the attacker just lurks until the user is authenticated. Keystrike, on the other hand, protects entire user sessions and thus other computers from being compromised.
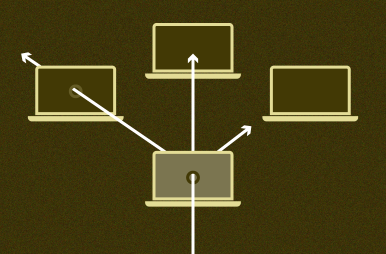
Lateral movement through impersonation
Even with modern authentication, it’s hard to distinguish between a legitimate user and an attacker with remote access to the workstation. Keystrike cryptographically proves that each keystroke and mouse click was physically made on the computer, effectively providing friction-free continuous authentication.

Ransomware
Attackers used RDP (Remote Desktop) connections in 95% of ransomware attacks in 2023. Keystrike Sanctum Guard insulates RDP connections from any unauthorized input.

Stealthy "living off the land" attackers
Rather than trying to infer malicious behavior—an impossible problem—Keystrike attests good behavior: that a command was intentionally made by a human on an authorized workstation.
Experience the true meaning of security
Curious how it all works? Keystrike Sanctum Guard ensures that commands are physically made on the employee workstation, in a manner that a remote hacker cannot forge. Watch our latest explainer video and discover the power of safeguarding user sessions with continuous authentication.